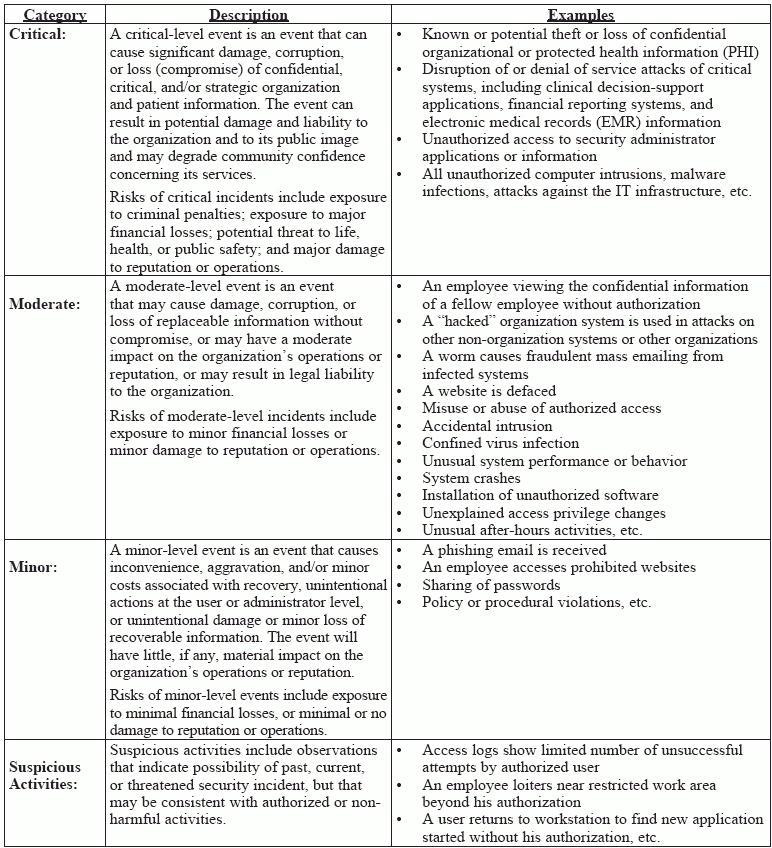
Know the risks at each incident level to prepare for the consequences.
An important first step to take when a security incident occurs is to determine the incident’s priority according to its impact. Security incidents may fall into one of three categories: critical, moderate, or minor. An incident may alternatively fall into a fourth category, “suspicious activities.”
“All critical incidents must be investigated and documented as incidents,” stresses Jim Sheldon-Dean, principal and director of compliances services for Lewis Creek Systems LLC based in Charlotte, VT. Moderate or minor incidents require minimal investigation and documentation as incidents, “but will receive full investigation and documentation if it is deemed that the incident is unusual and can be learned from so that similar incidents may be prevented in the future.”
For suspicious activities, you don’t need to conduct a detailed investigation and document them as security incidents, Sheldon-Dean says. But you may need to elevate a suspicious activity to a higher level, depending on the incident.
Use the chart below, courtesy of Sheldon-Dean, to help categorize security incidents: